BYOTee presents an innovative approach to creating customized Trusted Execution Environments (TEEs) using System-on-Chip (SoC) FPGAs. This architecture offers several key security advantages over traditional TEE implementations like Intel SGX and ARM TrustZone.
The BYOTee architecture achieves strong isolation through:
- Dedicated Hardware Resources - Each enclave gets its own dedicated softcore CPU, BRAM memory, and peripherals, eliminating resource sharing that could lead to side-channel attacks.
- Circuit-Level Isolation - The hardware resources within an enclave are connected but isolated at the circuit level from the hardcore system and other enclaves.
- Secure Memory - The use of BRAM instead of DRAM makes cold-boot attacks significantly more difficult since BRAM decays faster and is hardware-initialized on power-up.
- Customizable TCB - The hardware Trusted Computing Base can be minimized to include only the components necessary for each specific application.
However, a few side-channel attack vectors remain:
- Power Analysis - Remote power side-channel attacks are possible through on-chip ring oscillator-based power monitoring. This can be mitigated by only loading authenticated and trusted enclave bitstreams without power monitors.
- Long Wire Attacks - Since multiple enclaves share FPGA hardware resources, side-channel attacks through FPGA long wires are possible between enclaves.
- Physical Probing - While BYOTee protects against software-based attacks, physical probing of the FPGA remains a theoretical attack vector, though quite difficult in practice.
- Xilinx HDL compromise - We can assume a situation where the Xilinx HDL system itself creates vulnerablities in the software defined TEE enclaves. This is severely complex to achieve however it can be mitigated by using open source alternatives to Xilinx such as YoSys (Yosys Open SYnthesis Suite :: About)
The architecture proves robust because it:
- Eliminates CPU/cache sharing between enclaves
- Provides true physical isolation through dedicated hardware
- Uses secure BRAM storage that resists cold-boot attacks
- Allows minimal, customized hardware TCB per application
- Establishes a dynamic root of trust through secure FPGA configuration
BYOTee’s hardware-based isolation approach through FPGAs provides strong security guarantees for sensitive applications. The remaining side-channel risks require sophisticated hardware attacks that are challenging to execute in practice and can be mitigated through custom SoC design that includes elements like PUFs, independent power monitoring channels and mitigation through long wire FPGA attacks. The architecture demonstrates how FPGAs can be leveraged to build more secure TEEs compared to traditional CPU-based approaches.
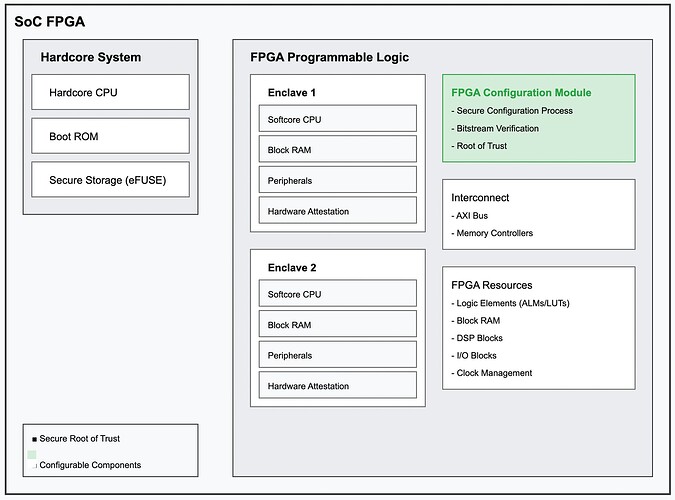
The key components of this SoC FPGA architecture:
1. Hardcore System
- Contains the hardcore CPU (e.g., ARM Cortex-A)
- Includes Boot ROM for secure boot
- Has secure storage (eFUSE) for device keys
- eFUSE should be upgraded to PUFs as we design our own SoC
2. FPGA Programmable Logic
- Houses multiple isolated enclaves
- Each enclave contains:
- Dedicated softcore CPU (e.g., MicroBlaze)
- Private Block RAM for secure storage
- Custom peripherals
- Hardware attestation module
3. FPGA Configuration Module (shown in green)
- Handles secure configuration process
- Verifies bitstream integrity
- Serves as root of trust
- Uses device keys for authentication
4. Interconnect
- AXI bus architecture
- Memory controllers
- Handles communication between components
- Enforces isolation boundaries
5. FPGA Resources
- Logic Elements (ALMs/LUTs)
- Block RAM modules
- DSP blocks
- I/O blocks
- Clock management
Key Security Features:
- Each enclave is physically isolated at the circuit level
- No shared resources between enclaves
- Secure BRAM storage resistant to cold-boot attacks
- Hardware-based attestation
- Secure configuration process
The architecture achieves security through physical isolation and dedicated hardware resources, making it significantly more resistant to side-channel attacks compared to traditional TEE implementations.
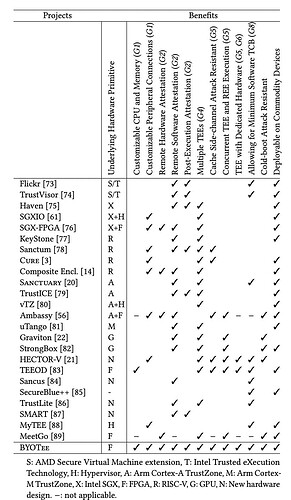
Key advantages of BYOTee compared to other TEE implementations by analyzing its improvements over each major solution.
Advantages over Intel SGX:
First, BYOTee solves one of SGX’s biggest limitations - the cache side-channel vulnerability. In SGX, the TEE and regular execution environment share CPU resources, including caches. This sharing creates opportunities for cache timing attacks, where attackers can infer sensitive information by observing cache access patterns. BYOTee prevents this by providing each enclave with its own dedicated softcore CPU and memory resources, eliminating resource sharing entirely.
Second, BYOTee offers better peripheral access control than SGX. In SGX, enclaves must trust the operating system to handle peripheral communications, which expands the trusted computing base unnecessarily. BYOTee allows direct, isolated paths between enclaves and their assigned peripherals, removing the OS from the trust boundary.
Advantages over ARM TrustZone:
TrustZone’s main limitation is its “all-or-nothing” security model - it provides only two security worlds with the secure world having complete control over the system. BYOTee improves on this in several ways:
First, it enables multiple independent secure enclaves rather than a single secure world. Each enclave has its own isolated environment with customized hardware resources. This supports the principle of least privilege much better than TrustZone’s model.
Second, BYOTee provides better isolation between secure and non-secure code. TrustZone’s secure world can access all system resources, including those of the normal world. In contrast, BYOTee enforces strict hardware-level isolation between enclaves and the rest of the system.
Third, BYOTee allows dynamic creation of secure environments at runtime, whereas TrustZone’s security configuration is static and determined at boot time.
Advantages over RISC-V KeyStone:
While KeyStone offers some hardware customization through RISC-V’s extensibility, it has several limitations that BYOTee addresses:
First, KeyStone’s hardware configuration is fixed at manufacturing time. BYOTee’s FPGA-based approach allows hardware resources to be customized at runtime, providing much greater flexibility in adapting to application needs.
Second, BYOTee provides stronger isolation guarantees. KeyStone relies on RISC-V’s Physical Memory Protection (PMP) feature for isolation, which still allows some resource sharing. BYOTee achieves complete physical isolation through dedicated hardware resources for each enclave.
Third, BYOTee offers better resistance to cold-boot attacks. KeyStone uses DRAM for secure memory, which is vulnerable to cold-boot attacks due to data remanence. BYOTee uses BRAM, which decays much faster and includes hardware initialization on power-up.
Universal Advantages:
Beyond these specific comparisons, BYOTee offers some unique advantages that apply across the board:
- Customizable Hardware TCB: BYOTee allows each enclave to have exactly the hardware resources it needs, no more and no less. This minimizes the attack surface compared to fixed-hardware solutions.
- Verifiable Design: Being FPGA-based, BYOTee’s hardware configurations can be formally verified, providing stronger security guarantees than proprietary hardware solutions.
- Post-Execution Attestation: BYOTee uniquely supports attestation of both inputs and outputs, allowing verification of computation results.
- Concurrent Execution: BYOTee enables true parallel execution of secure and non-secure code through physically separate processing units.
These advantages stem from BYOTee’s fundamental architectural choice of using FPGA to create physically isolated, customizable secure environments. This approach allows it to combine the security benefits of hardware isolation with the flexibility of software-defined systems, while avoiding many of the vulnerabilities present in traditional TEE implementations.
Plan of Action:
- Implement the BYOTee framework on a commercially available FPGA SoC like the one in the link below:
[https://robu.in/product/cora-z7-zynq-7000-single-core-arm-fpga-soc-board/?gad_source=1&gclid=CjwKCAiAk8G9BhA0EiwAOQxmfsqVf2RahRkkaspOTrTcgciMhBzwIfwaAv2mgVRFv2K1Xo5pSoAwShoCie8QAvD_BwE] - Distribute 2 boards to the software team to develop and test various TEE enclaves and test their functionalities.
- Distribute 2 boards to security teams to test various side channel attack vectors and identify hardware vulnerabilities
- Distribute 1 board for developing the BYOTee framework to adapt from close source Xilinx HDL to Opensource HDL frameworks like YoSys (Yosys Open SYnthesis Suite :: About). Here we need to make sure that FPGA usage is as optimized as a Xilinx HDL output.
- From the output of the three things above, we can build on a solid foundation of FPGA SoC with a clear roadmap of our hardware design, hardware security features, FPGA and the TEE HDLs which can be taken to the semiconductor foundry
Moderator edit: Paper link