The Trustless TEE Initiative is a public goods effort that seeks to enable low-latency confidential computing. Our approach is bottoms-up, starting at the silicon. In a data-driven world, motivation for confidential computing can be drawn from many use cases, however the rapid rise of AI is the most poignant indicator of the criticality of our mission. Given the immediacy of the need for this kind of technology, as well as high performance requirements, remotely-attested secure hardware stands out amongst alternatives as the most promising route to secure confidential computing - thus, secure hardware is our current focus.
Although the notion of secure hardware is not novel, the TTEE direction is unique in our pursuit of both high performance and a comprehensive security model. In contrast, edge devices like credit cards have achieved high security, but traded off performance and functionality due to heavy limitations on power and area. Existing TEE products like Intel SGX or AMD SEV, have prioritised high performance and attempted to add security onto unsuited hardware and without the use of theoretically grounded security measures or a comprehensive physical threat model. Very few approaches have leveraged the hardening power of open-source design, and none have publicly addressed the implied supply chain security assumptions. Thus, TTEE sets out to fill a critical gap.
Why now?
As much as progress in AI and increased societal digitisation pose an ever-increasing need, we have never before been as well equipped to meet this need. Recent advancements in open hardware across tooling, IP and foundry participation allow for faster iteration, public audits and more experiments. At the same time, recent advances in academic spheres have led to the development of theoretical foundations and automated tools that drastically reduce the complexity of designing secure hardware and allow for the same principled reasoning that has underpinned the development of cryptography in past decades. These developments instill confidence that we have success within our reach.
Challenges
Success in this mission entails overcoming three obstacles:
- Supply chain security: Unlike software solutions which can be easily subjected to public audits, hardware security measures also have physical instantiations which must be verified as correct. The existence of secure designs is meaningless if the presence of entailed defenses cannot be assured.
- Physical security: Invasive key extraction, physical side channels and fault injection attacks are all serious attack vectors. While there exist promising defenses against these attacks, a historic emphasis on secrecy and obscurity has prevented the public identification of the most promising techniques.
- Practicality and usability: As we’ve learnt with other technologies, security alone does not make meaningful impact. Adoption demands usability. In the case of TTEE, navigating the tradeoffs between security and performance for various use cases is the foremost challenge.
Goals
All three of these challenges must be tackled in parallel. From the challenges, we derive three tracks with the ultimate goal of combining these into comprehensively secure hardware. For each track, we identify an initial goal:
- Establish a dual design & inspection protocol for the prevention of trojans that has a clear path to scaling and hardening. Crucially, we are not only pursuing mechanisms for detecting deviations in physical chips, but also protocols for performing audits that are credible to third parties.
- Demonstrate the possibility of fully securing hardware. Historically, hardware designs have leaned on obscurity as a means to security. Large companies have also employed legal threats to prevent academic or public audits of their defenses. This has made verifying the strength of various countermeasures nigh impossible. Against this backdrop, it is necessary for us to publicly prove that a system leveraging state-of-the-art techniques can indeed be secured against a powerful attacker. This must be done by giving attackers sufficient incentive and the best possible tools to attack the system, including publishing all design material.
- Develop a flexible hardware system that successfully serves use cases with non-trivial performance requirements while maintaining sufficient levels of physical security. Such a design must draw on existing literature and publish design artifacts to ensure that lessons in security and identified performance bottlenecks can be carried forward into future iterations in a systematic and principled way.
Cornerstone Technologies
Realising these goals will leverage a wide range of tools and techniques. Among these, a few cornerstone technologies have been identified as initial focus areas.
- Physical Unclonable Functions (PUFs) serve two important functions. They provide a key generation and storage method that does not require key injection, removing a critical supply-chain attack vector. Tamper sensitivity also means that PUFs constitute a defense against invasive attacks that physically alter the chip.
- Composable cryptographic masking schemes, especially prime masking, promise to provide essential defense against side channel and fault injection attacks. Composability properties help to reduce the complexity of security arguments, and tools designed to verify the correctness of masking implementations dramatically reduce risk.
- Infra Red In Situ (IRIS) is a method for non-destructive imaging intended for trojan detection. While substantial complementary research on design principles still needs to be done, the existence of a reliable and low-cost way to detect trojans points to the viability of scalable, decentralised auditing.
Big Picture Plan
The first priority is to initiate work focused on hardware defense against physical adversaries. Doing this in an open-source manner already begins to reduce surface area for trojan attacks, removing especially vulnerable vectors such as opaque firmware. In order to accomplish this, several projects will be launched in a first wave.
After this first wave has been set in motion, our focus must also encompass supply chain attacks. An important part of this is supporting the development of low-cost, non-destructive imaging techniques like IRIS. Additional research into complementary design techniques is also a key contribution which the academic community is best poised to deliver. This work should culminate as a first milestone into a trojan-detection protocol that is applied to chips produced at the completion of first wave projects (estimated 2.5 years from launch). For more on supply chain attacks, see this post.
A later focus, must consider the developed experience of safely using this secure hardware. Several works have already laid the foundation of this direction [1,2].
First-Wave Projects
In order to move toward our goals and facilitate the development of these technologies, three high-impact projects are being undertaken, with the intention of adding more in the near future. We intend to add several smaller projects with shorter time horisons as soon as these large projects are underway.
Indestructible PUF Signer
This project aims to demonstrate the possibility of fully securing a physically instantiated key against the most powerful attackers. The design will be fully open source and all barriers to attacking the delivered chips will be removed and incentive for attempting these attacks will be provided in order to ascertain the strength of the intended security claim. The project will make use of PUF(s) for key generation and storage and to defend against invasive attacks. State-of-the-art, theoretically-sound masking will be used to protect a post-quantum secure signing algorithm with the intention that this approach can be reused in future designs.
The project can be viewed in two phases. In the first phase, parallel development of a weak PUF and hardened signing logic will take place. In the second, the PUF and signing logic will be combined and subject to heavy testing.
Time to completion: 3 years + 1 year red teaming
Cost: 1.5M
PUF MPW Experiments
Currently, there is no production-ready open-source PUF design available. Developing this IP involves some trail-and-error which, on open foundries, can take a very long time if done sequentially. By providing access to multi-project wafer runs and small grants, this project parallelises the testing of various approaches and increases the chances of success of the PUF Signer project, which depends on the successful development of an open source PUF.
Time to completion: 3 years + 3 mo red team
Cost: variable (0.5-1M)
Next-Gen TEE
This project seeks to use existing research to build a production-ready TEE. Successful deployment of this TEE will serve both as an immediate improvement over existing solutions, and to illuminate key improvement areas where more research or development work must be focused, especially as multiple security techniques must be combined. In contrast to the PUF Signer project, the next-gen TEE must address the complex task of full microarchitectural security, including protections of memory, as well as incorporating some of the same masking and redundancy approaches as the signer project. This project will be driven by Fabric Cryptography.
While the overall project will take several years (~3) and an estimated $20M, it should be started with a feasibility study to determine the viability of various techniques and the project overall. This study will employ pseudo-cycle accurate simulations and PPA estimates to understand the performance and cost of various design and manufacturing approaches for a list of sample use cases. It should also contain qualitative assessments of the time and human resources required to implement various countermeasures.
Time to completion: 6-9 months (feasibility study)
Cost: 2M
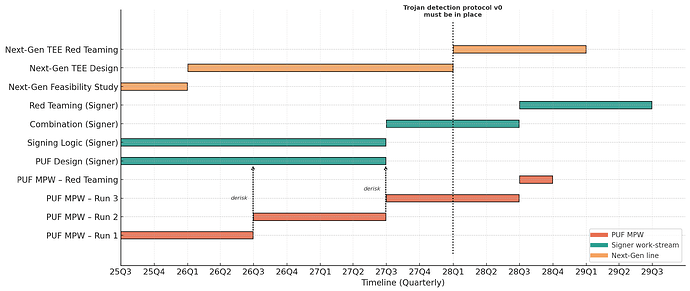
First-Wave Timelines
[to be updated as project timelines are finalised]
Technical Challenges
Supply Chain
Technical challenges for supply chain attacks are explored in depth in this post.
Physical Security
Achieving physical security is broken down as follows:
- Prevent attackers from physically altering the chip. PUFs are a key focus for this reason, but other tamper-detection technologies also exist. For example, it should not be possible for the attacker to inject many permanent faults via laser, nor should the attacker be able to shave away significant amounts of silicon from the die backside without destroying secrets.
- Given 1 is achieved, physical side channel and fault injection attacks are the next focus.
- Side channels attacks (e.g. DPA, EM and optical scanning) are to be mitigated using masking technologies. These technologies split computations (”MPC on a chip”) to amplify noise levels. While some of this masking can be done at a software level, the hardware must at minimum be designed to enable this and, ideally, to accelerate it. Apart from designing masked instructions, the microarchitecture and low level firmware must also be designed to preserve masking protections (e.g. by preventing shares of the same secret being written to the same register or frequently refreshing random masks to keep signal-to-noise ratios low).
- Fault injection attacks are circumvented by combining two countermeasures. On the one hand, masking and redundancy requires the attacker to inject multiple precise and coordinated faults to pull off a successful attack. One the other hand, the use of sensors make large interventions untenable for the attacker. The most challenging case to address is the combined use of faults and side channel probing, which has thus far not been widely studied.
- At a similar level of importance to side channels and fault injection, memory protections must be put into place. This entails using memory encryption and memory integrity so that an attacker can neither learn valuable information from knowing the state of off-chip memory, nor inject old or counterfeit values. Successfully implementing this requires dedicated on-chip memory to store a commitment to the correct state of memory.
Correctly addressing these three challenges (and all the omitted related details), leaves us with a chip that ensures that for any given sequence of instructions, an attacker should not be able to learn the data being operated on or undermine the integrity of the computation apart from preventing its success. In addition to these properties, the following are helpful but not strictly necessary countermeasures:
- Hardware support for oblivious data structures: even though values stored in memory might be encrypted, an attacker can critically still ascertain which locations are being accessed and when. Oblivious data structures (e.g. ORAM) prevent the attacker from learning what values were accessed. While its possible to implement this at the software level given enough on-chip memory, the overhead of these kinds of mechanisms can be reduced with clever design. Additionally, access to memory can be batched, delayed and supplemented with dummy accesses so as to avoid leaking information due to the timing of accesses. The same can be done for networking.
- In addition to preventing the attacker from learning what data an operand is operating over, we can also prevent the attacker from telling what operand is being executed at all. The easy version of this is to make instructions or classes of instructions execute for the same amount of time (or provide the software language to specify this). However, for attackers that are able to monitor other channels such as power consumption, additional countermeasures must be employed. Successful implementation of such equivalence classes make it much easier to hide inputs to complex programs with lots of branching or even hide the algorithm itself.
Without implementing 4 and 5, a lot of overhead and complexity is left to software mitigations. Mitigations 1-3 can protect fixed sequences of operations, but the algorithm designer still needs to make sure that their program always is executed as a fixed sequence of instructions or that variations in the sequence of instructions does not leak key information. With 4 and 5 implemented, software mitigations must still be realised, but the overhead and complexity of doing so is much reduced.